- An analysis of ceramic tool condition monitoring for enhanced and secured manufacturing
Thirumalai Ramanathana,* and Vivekraj Mb
aProfessor, Mechanical Engineering, Dr.N.G.P. Institute of Technology, Coimbatore, India
bResearch Scholar, Mechanical Engineering, Dr.N.G.P. Institute of Technology, Coimbatore, IndiaThis article is an open access article distributed under the terms of the Creative Commons Attribution Non-Commercial License (http://creativecommons.org/licenses/by-nc/4.0) which permits unrestricted non-commercial use, distribution, and reproduction in any medium, provided the original work is properly cited.
In metal cutting tool wear is complex phenomenon which occurs in several ways and it could not be avoided. Due to the high tool wear rate the close dimensional accuracy of the parts are not achieved and as a result the manufacturing execution system fails in sending secured data to the systems properly. High security data transmission is essential in manufacturing execution system. Various algorithms are used for cryptography in the today’s market for securing the data. This paper employs a ceramic tool for machining Inconel 718 to obtain close dimensional tolerance and thereby enhancing the secured data transfer effectively. The novelty of the work is incorporating the ceramic tool in the turning process and there by improving the secured data transmission in the industrial automaiton. The outcome of the work is to measure the accuracy and precision of the machined parts from the ceramic cutting tool and to find the comparative improvement in the usage of several algorithms used in enhanced secured data transmission
Keywords: Ceramic tool, Inconel 718, Secured Manufacturing, ANOVA, Tool wear
Tool wear plays an important role in achieving closed dimensional accuracy. The reduction in tool wear will improve the manufacturing processes and there by the precison in manufacturing can be obtained. This research work uses a ceramic cutting tool with nose radius of 102 mm to turn Inconel 718. The ceramic tool posses high melting point, high chemical stability, high tem- perature resistance, high oxidation rate and high hardness. Due to these properties, the ceramic tools are used widely by the industrialist to turn the nickel based alloy Inconel 718. The process parameters selected in this work are speed, feed and depth of cut. The values of the process parameters are selected based on the litera- ture review. The tool wear is selected as a response in this research work and the tool wear is measure using advance optical microscope to measure the amount of wear after particular hours of machining the work piece Inconel 718. The cross hairs of the microscope are used to measure the tool wear. The ceramic tool provides high precision and accuracy of the parts manufactured during the machining process. Nowadays, the automobile industries are oriented towards high precision and accuracy and most of the industries are moving towards Industry 4.0, there by transferring secured data trans- mission between the terminals. In this way the accuracy and precision is most important to achieve the in- dustrial automation and the usage of the ceramic tool will brings in this facility and improves the security enhancement.
Ceramic tool exhibits high hardness and are promis- ing with high mechanical and tribological parameters. The precision are measured using the standard deviation calculated from results obtained by carrying out replicate measurements on measuring hardness and tool wear in machining Inconel 718 under prescribed conditions.
Due to this the automation process are highly benefitted without any disturbances in industrial automation 4.0. Industrial automation involves in bringing the high precision in manufacturing and also transferring secured data from one system to the other system. Inconel 718 is a heat resistant super alloy (HRSA), which maintains an excellent mechanical strength at elevated temper- atures, typically between 7000C and 11000C. Machining parameter and tool geometry are the important parameters that affects the machinability properties. A machinability is the functional relationship between the input parameters and the output responses of machining process. Cipher text refers to conversion of a message to a random cipher text through secret writing techniques known as Cryptography. Cryptographic algorithm is referred to secret-key algorithm, which makes it impossible to view the datas that are transferred from one end to another without processing with a secret key. This secret key used for safety transformation of the data is used for both encryption and decryption. Only authorized entities can manage these secret keys for bringing up its performance and efficiency. The secured conventional encryption should be an opponent, which is unable to decrypt cryptogram or discover the key. The secrecy of the key is most important than the secrecy of the algorithm in securing the conventional encryption scenario. If the correspondent and the user use the same key then it is regarded as similar cryptosystem whereas if the receiver and sender make use of different keys, then it is referred to as public-key cryptosystem. A collection of cipher processes input block continuously and produces the output element at every time. In a caeser cipher encryption-decryption system, the numerical equivalent is assigned to each alphabet and maximum number of possible keys is generated.
Different coated tools are used to conduct several experiments working with several cutting conditions on Inconel 718 are investigated [1]. The process parameters chosen are cutting speed, feed and depth of cut. The cutting forces and feed cutting forces are investigated for the orthogonal cutting process. The cutting ratio is also calculated to measure the tool wear. A mathematical correlation between the toolwear and spindle poser is estimated in the semi dry cutting cutting conditions while turning of inconel 718 [2]. Lower cutting force, flank wear and less cutting temperature are obtained due to the selection of optimum cutting parameters and effective lubrication systems available. The increase in coolant pressure will normally increases the tool life. The productions of chip segmentation are not produced with les supply of coolant pressure. The vibrations in 3D high speed finish turning and the effect of tool edge wear are investigated. The cutting forces on nickel based super alloy Inconel 718 are also investigated [4]. Excellent material toughness is inhibited for Inconel 718. The difficulty in chip breaking during the process is becoming a very tedious process while turning Inconel 718. Hence high tool wear is noticed and this results in lower material removal rate and poor surface finish [5-6].
Reviews on the cryptography for IoT based applications are carried out to address the security and privacy. In this case the substantiation plays an prominent role along with data integrity [7]. It is noticed that major concern for security concern is to resist attacks such as forgery, ciphertext attacks and so on. Internet of things observe the surroundings environment and extend support to transfer important and confidential data over the Internet without any obstacles from the human beings. End-to-end security is acquired by using object security and lightweight encryption [8]. The goals of the security layer are well defined considering network segmentation. Industry 5.0 uses Industrial IoT for achieving decentral- ization, higher connectivity, and better interoperability. Attribute credential infrastructure based cryptography is developed since existing public key infrastructure based cryptography [9]. The additive manufacturing with block chains are investigated with enhanced security. These block chains used for the security are distributed with physically un-clonable functions [10]. Block chain enables the tracking and recording of all the transactions taking place in a manufacturing scenario in cloud environment could not be altered. The authors proposed complete security by making the devices as tamper resistance hardware and peripheral devices. Cryptography algorithm is optimized for efficient data security on cloud computing [11]. The cloud providers have problem with the security while processing and transferring information’s from one end to the other and there are more possibility for misuse, illegal viewing of data and losing the data during these processes. Cryptography is suggested for safety method of data transfer and storage protection. Blowfish is used to build a cross-functional algorithm and provides high safety and confidentiality for data transfer. The threats and prospects of high quality and precise manufacturing which is used for manufac- turing high precision micro components are described [12]. Ultra precision manufacturing industries employs Industrial Internet of Things to provide sustainability and technology advancements to increase the production volume. Ultra precision manufacturing incorporates preliminary framework for IoT techniques and supple- ments this technique to all the industries and academic professionals to develop further. Cloud manufacturing is developed for smart diagnosis services [13]. Process monitoring tasks between different resources are shared by the proposed architecture. Diagnosis on tool condition is provided as cloud service using sensor and network communication. On this data provided by the cloud, the proper corrective actions are taken and the tool perfor- mance is monitored in the manufacturing environment. Cloud enabled prognosis is suggested for manufacturing thereby providing new goals for advanced manufactur- ing [14]. Several strategies for cloud computing are discussed and cloud enabled prognosis for production are well defined. Tool failure detection system using sensors placed at multiple points are developed and sensor fusion algorithm is integrated to the machine diagnosis to make suitable decisions on tool monitoring systems [15]. Usually a single sensor is used to study the tool breakage in a machining environment but in this work multi sensor has been put forward to improve the consistency of tool breakage signatures derived from a machine interface. The performance analysis of the various cryptographic algorithm such as DES, AES and Blowfish are analysed and then compared [16]. Orthogonal array is used to conduct 27 experiments and grey relational analysis is used for multi objective optimization and selection of optimum drilling parameters [17].
The 3-D printing technologies involve high level of security in the process of fabrication and manufacturing processes [18]. The wear behavior of titanium powder reinforce with carbon nanotubes are investigated [19].
To investigate the performance of tool wear in Inconel 718, single pass turning operation is carried out in dry condition. The experiments are carried out in a CNC lathe with the following specifications; : Power, 15 KW motor drive, and speed range: 0 - 3500 rpm, and feed range: 0.01 - 100 mm/rev. The Scanning electron microscope is used to observe tool wear and record it by INCA PentaFETx3. Rockwell hardness testing machine is used for measuring the hardness of the samples turned using ceramic tool.
In this research, ceramic tools are used to machine Inconel 718 in order to find the appropriate cutting conditions. Ceramic insert (TNMG 160408 A65) with tool holder is used for this investigation. The experiment is conducted on automatic lathe. The wear of tool insert was measured using Tool maker’s Microscope. The objective focus of this work has been to find most dominant feature of tool wear with ceramic insert with dry machining. Experiments have been conducted at four cutting parameters (speed, feed rate, depth of cut and hardness) with three levels for each cutting parameter and the experimental data are presented in Table 1.
In the existing network, the data transmission time is calculated using several cryptographic algorithms and these are examined. In DES, key length is bits and block size is 64 bit length. Tool failure detection system using sensors placed at multiple points are developed and sensor fusion algorithm is integrated to the machine diagnosis to make suitable decisions on tool monitoring systems [20]. Usually a single sensor is used to study the tool breakage in a machining environment but in this work multi sensor has been put forward to improve the consistency of tool breakage signatures derived from a machine interface. Several researchers investigated the Multipass machining based on cloud computing and discussed the optimization of the processes [21]. The performance analysis of the various cryptographic algorithm such as DES, AES and Blowfish are analysed and then compared. The comparison of the performance of the algorithm under different loads based on the parameters: key size, block size and speed. Java pro- gramming is used for simulating the program. DES, Data encryption standard uses 56 bit key and maps 64 bit input lock into a 64 bit output lock. AES, Advanced encryption standard is a symmetric block cipher that can encrypt data blocks of 128 bits using symmetric keys 128,192 or 256. Blowfish is a symmetric block cipher, in which key varies from 32 bits to 448 bits and provides secured data transmission. The comprehensive cryptographic algorithms such as DES, 3DES, AES, RSA and Blowfish are analysed.
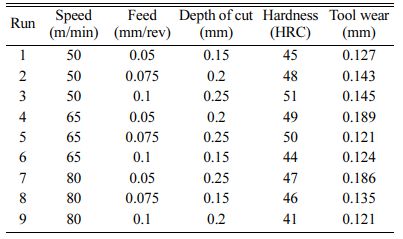
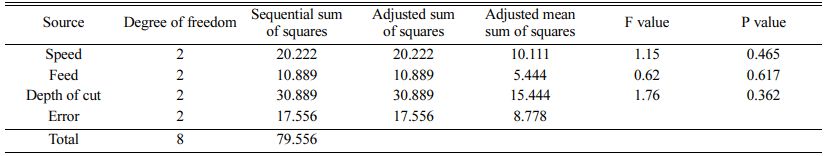
ANOVA analysis is carried out and it is seen that the R-squared value for hardness is 78% and R-squared value for the Tool wear is 68% and they are presented in Table 2 nd 3 respectively. From this tables it is evident that all the parameters considered in this work are more significant.
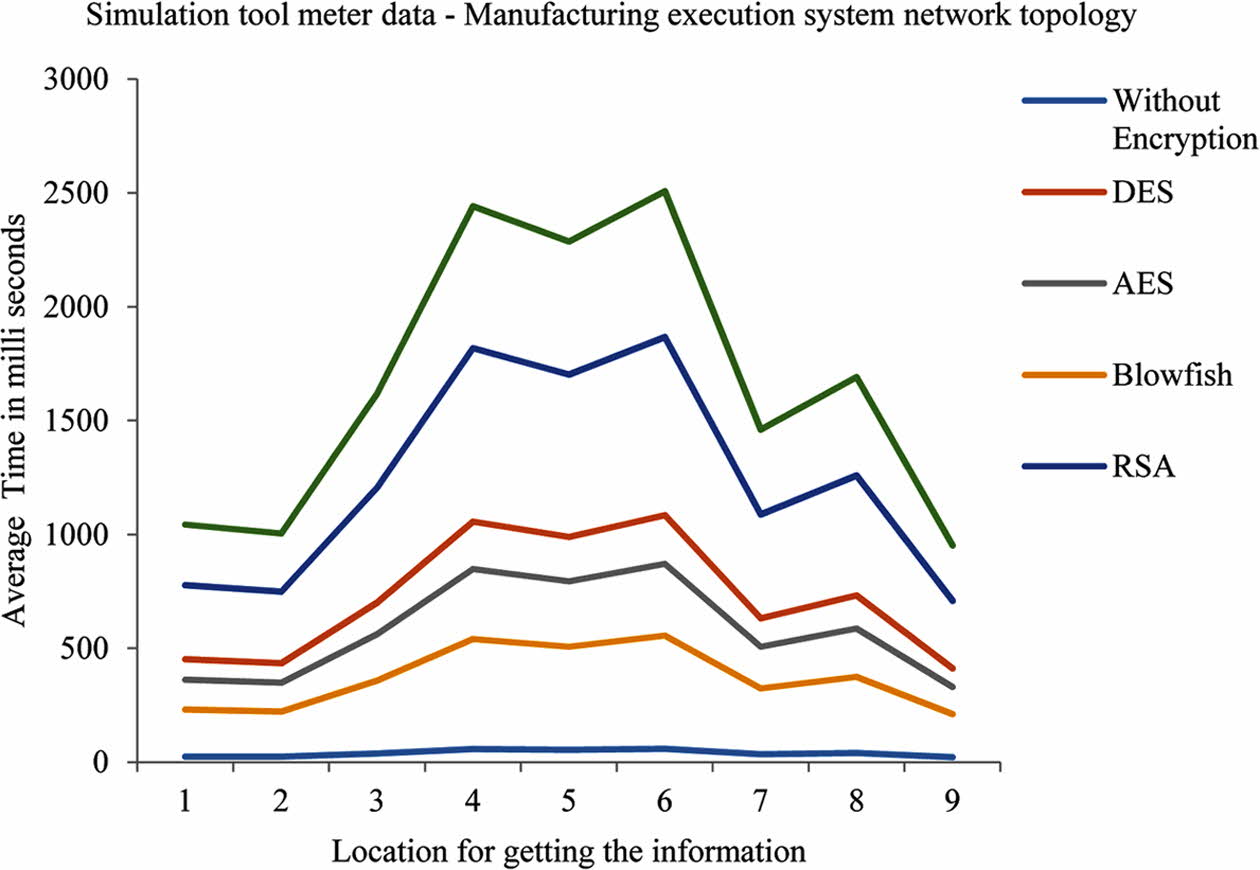
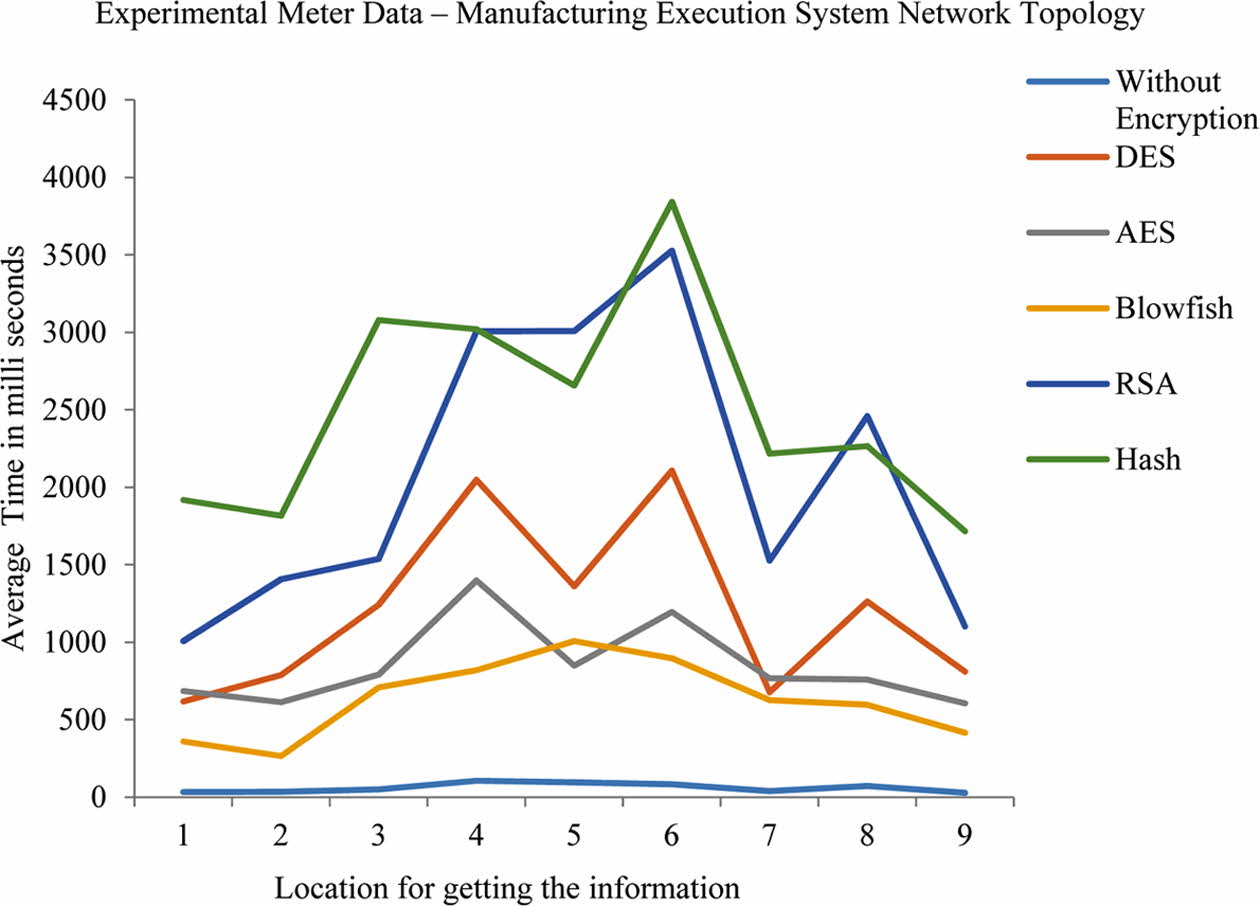
The significant features are found to be feed rate and hardness and most influential. Furthermore the depth of cut and the harness of the ceramic tool seems to be less contributory function when compared to the other parameters selected for the analysis of the tool wear. The platform Linux and Mac Os are chosen for running these optimal tools. The simulation tool will run on the following simulation softwares; GNS3, NS3 and OMNET++. The dynamic routing protocol EIGRP is used to assign the destinations automatically in the routing table of the individual routers. When compared with the static routing protocols, this EIGRP protocol provides simplest and efficient routing. The dissimilar authentication passwords are provided at each time and thereby it is noticed that EIGRP provides advanced security features. In this paper cryptographic algorithms such as DES, AES, Blowfish, RSA and Hash are in- vestigated and compared successfully. The assembling execution framework datasets comprises of different hubs and servers. The master frame work get sufficient information’s from these hubs and servers. The average time to transfer a message in a manufacturing execution system when using a simulation meter is compared with several cryptographic algorithm. It is seen from Fig. 1 that data transmission average time taken by the Blowfish is minimum with 211.15 ms whereas the data transmission time taken by Hash is the maximum with 952.02 ms. Similarly, the Fig. 2 shows the the average time to transfer a message in a manufacturing execution system when using an experimental meter. It is seen that data transmission average time taken by the Blowfish is minimum with 415.96 ms whereas the data transmission time taken by Hash is the maximum with 1716.93 ms. In any manufacturing execution system, the security in data transmission is considered with the strength in the data transfer and hence it is concluded that Hash provides the better security when compared to the other cryptographic algorithms.
|
Fig. 1 Simulation tool meter data - manufacturing execution system network topology. |
|
Fig. 2 Experimental meter data - manufacturing execution system network topology |
The analysis of tool wear in turning inconel 718 is investigated using a ceramic tool. It is concluded that the tool wear is very minimum and it is under the close dimensional tolerance and provides excellent machin- ability. Because of this enhanced accuracy and precision in the usage of the ceramic tool, the security is very high when used in the automation industries. In the advanced manufacturing scenario the most demanding feature in network relevance is high security in data transmission. The high confidential data’s are shared nowadays in a manufacturing executions system en- vironment over the internet are increasing nowadays. This gives an interesting subject for the researchers to provide best solution for secured data transmission to offer protection against the data intruders attack in the manufacturing execution system. This paper compares the transmission time required for implementation using several cryptographic algorithms. From the results, it is observed that the blow fish cryptographic algorithm provides the minimum time for the data transmission while the hash cryptographic algorithm provides the maximum time for the data transmission. It is concluded that Blowfish is the optimum choice for the users who prefer minimum time for the data transmission. However, Hash cryptographic algorithm consumes maximum time for the data transmission. But in terms of level of security hash algorithm is preferred over blowfish algorithm. The future scope of this work can be extended to all industrial automation for improved the secured data transmission system and improving the productivity of the industries.
- 1. A. Devillez, F. Schneider, S. Dominiak, D. Dudzinski, and D. Larrouquere, Wear. 262[7] (2007) 931-942.
-
- 2. D.G. Thakur, B. Ramamoorthy, and L. Vijayaraghavan. Int. J. Adv. Manuf. Technol. 50[5-8] (2010) 471-478.
-
- 3. E.O. Ezugwu and J. Bonney, J. Mater. Process. Technol. 153 (2004) 1045-1050.
-
- 4. N. Fang, P.S. Pai, and S. Mosque, Int. J. Adv. Manuf. Technol. 52[1-4] (2011) 65-77.
-
- 5. I.A. Choudhury and M.A. El-Baradie, J. Mater. Process. Technol. 77 [1] (1998) 278-284.
-
- 6. M. Rahman, W.K.H. Seah, and T.T. Teo, J. Mater. Process. Technol. 63[1] (1997) 199-204.
-
- 7. V. Rao and K.V. Prema, J. Ambient Intell. Humaniz. Comput. 12[9] (2021) 8835-8857.
-
- 8. A. Mosteiro-Sanchez, M. Barcelo, J. Astorga, and A. Urbieta, J. Manuf. Syst. 57 (2020) 367-378.
-
- 9. X. Yao, H. Kong, H. Liu, T. Qiu, and H. Ning, IEEE Trans. Industr. Inform. 15[4] (2019) 2297-2307.
-
- 10. B. Cambou, M. Gowanlock, J. Heynssens, S, Jain, C, Philabaum, D, Booher, I. Burke, J. Garrard, D. Telesca, and L. Njilla, J. Cryptol. 4[2] (2020) 17.
-
- 11. M. Buvana, Turk. J. Comput. Math. Educ. 12[2] (2021) 459-464.
- 12. W.S. Yip, S. To, and H. Zhou, J. Intell. Manuf. (2021) 1-13.
-
- 13. A. Caggiano, Int. J. Comput. Integr. Manuf. 31[7] (2018) 612-623.
-
- 14. R. Gao, L. Wang, R. Teti, D. Dornfeld, S. Kumara, M. Mori, and M. Helu, CIRP Annals 64[2] (2015) 749-772.
-
- 15. J.-D. Kim and I.-H. Choi, Int. J. Mach. Tools Manuf. 36[8] (1996) 861-870.
-
- 16. J. Thakur and N. Kumar, Int. J. Emerg. Technol. 1[2] (2011) 6-12.
- 17. M. Srinivasan, S. Ramesh, S. Sundaram, and R. Viswanathan, J. Ceram. Process. Res. 22[3] (2021) 345-355.
-
- 18. I. Topcu, J. Ceram. Process. Res. 22[2] (2021) 143-148.
-
- 19. M. Ceylan and I. Topcu, J. Ceram. Process. Res. 21[5] (2020) 539-546.
-
- 20. J.D. Kim and I.-H. Choi. Int. J. Mach. Tools Manuf. 36[8] (1996) 861-870.
-
- 21. M. Chandrasekaran, M. Muralidhar, and U.S Dixit. Int. J. Adv. Manuf. Syst. 65[1-4] 239-250.
-
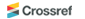
 This Article
This Article
-
2022; 23(2): 228-232
Published on Apr 30, 2022
- 10.36410/jcpr.2022.23.2.228
- Received on Dec 7, 2021
- Revised on Dec 27, 2021
- Accepted on Jan 10, 2022
 Services
Services
- Abstract
introduction
literature review
methodology
results and discussion
conclusion
- References
- Full Text PDF
Shared
 Correspondence to
Correspondence to
- Thirumalai Ramanathan
-
Professor, Mechanical Engineering, Dr.N.G.P. Institute of Technology, Coimbatore, India
Tel : +91 9843240635 - E-mail: vkrthirumalai@gmail.com






 Copyright 2019 International Orgranization for Ceramic Processing. All rights reserved.
Copyright 2019 International Orgranization for Ceramic Processing. All rights reserved.